67. Topic 2, Litware, Inc
Overview
Litware, Inc. is a financial company that has 1,000 users in its main office in Chicago and 100 users in a branch office in San Francisco.
Existing Environment
Internal Network Infrastructure
The network contains a single domain forest. The forest functional level is Windows Server 2016.
Users are subject to sign-in hour restrictions as defined in Active Directory.
The network has the IP address ranges shown in the following table.
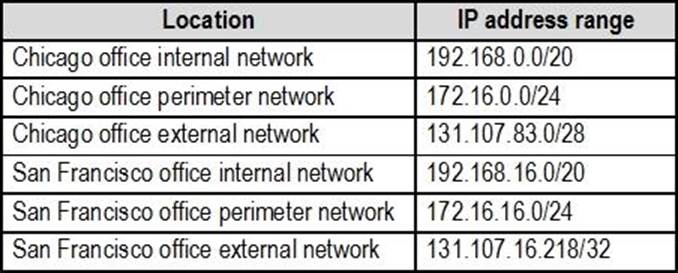
The offices connect by using Multiprotocol Label Switching (MPLS).
The following operating systems are used on the network:
✑ Windows Server 2016
✑ Windows 10 Enterprise
✑ Windows 8.1 Enterprise
The internal network contains the systems shown in the following table.
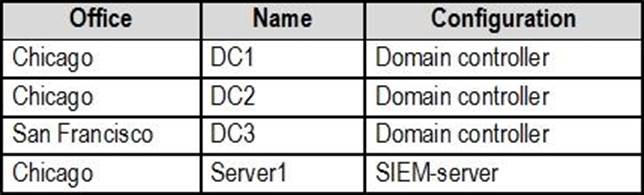
Litware uses a third-party email system.
Cloud Infrastructure
Litware recently purchased Microsoft 365 subscription licenses for all users.
Microsoft Azure Active Directory (Azure AD) Connect is installed and uses the default authentication settings. User accounts are not yet synced to Azure AD.
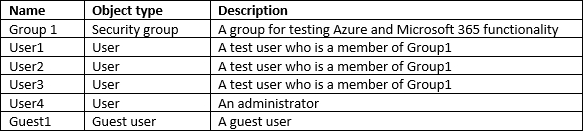
You have the Microsoft 365 users and groups shown in the following table.
Planned Changes
Litware plans to implement the following changes:
✑ Migrate the email system to Microsoft Exchange Online
✑ Implement Azure AD Privileged Identity Management
Security Requirements
Litware identities the following security requirements:
✑ Create a group named Group2 that will include all the Azure AD user accounts. Group2 will be used to provide limited access to Windows Analytics
✑ Create a group named Group3 that will be used to apply Azure Information Protection policies to pilot users. Group3 must only contain user accounts
✑ Use Azure Advanced Threat Protection (ATP) to detect any security threats that target the forest
✑ Prevent users locked out of Active Directory from signing in to Azure AD and Active Directory
✑ Implement a permanent eligible assignment of the Compliance administrator role for User1
✑ Integrate Windows Defender and Windows Defender ATP on domain-joined servers
✑ Prevent access to Azure resources for the guest user accounts by default
✑ Ensure that all domain-joined computers are registered to Azure AD
Multi-factor authentication (MFA) Requirements
Security features of Microsoft Office 365 and Azure will be tested by using pilot Azure user accounts.
You identify the following requirements for testing MFA.
✑ Pilot users must use MFA unless they are signing in from the internal network of the Chicago office. MFA must NOT be used on the Chicago office internal network.
✑ If an authentication attempt is suspicious, MFA must be used, regardless of the user location
✑ Any disruption of legitimate authentication attempts must be minimized
General Requirements
Litware want to minimize the deployment of additional servers and services in the Active Directory forest.
You need to create Group2.
What are two possible ways to create the group?

Schreibe einen Kommentar